Privacy+Verifiable Echo➜
PrivEcho
Creating value at the intersection of privacy and verifiability.
Key Features
Privacy Protection
Advanced cryptographic techniques ensure your data remains private and secure at all times.
Verifiable Computing
Transparent and verifiable computation results without compromising data privacy.
Decentralized Security
Leverage blockchain technology for enhanced security and transparency in your applications.
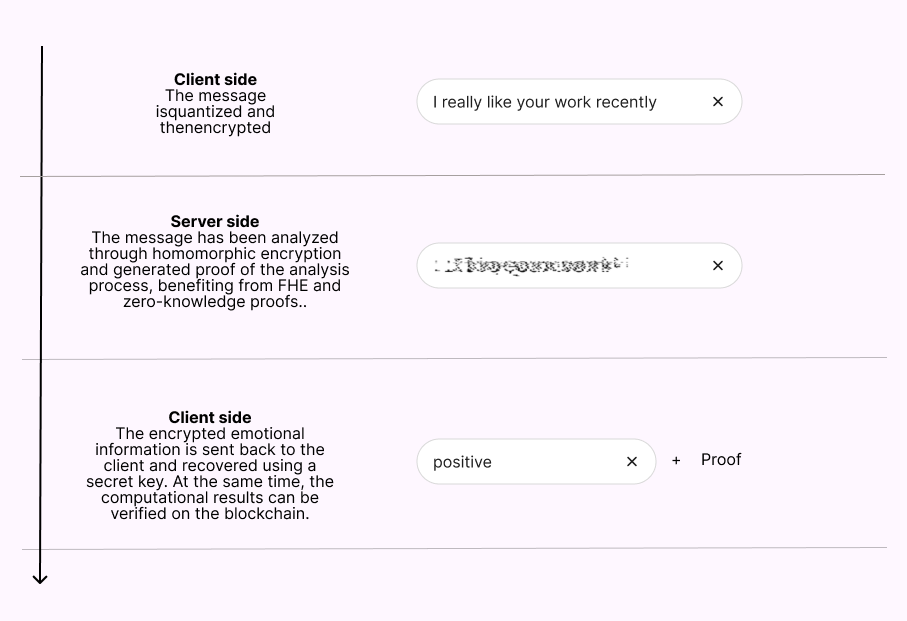
How PrivEcho Works

1Fee Payment
The demand side initiates the process by paying the required fee.
2Data Encryption
Original data is encrypted by the demand side to ensure privacy.
3Request Initiation
The demand side uses the encrypted ciphertext to initiate a request.
4PrivEcho Processing
PrivEcho schedules the requests and generates zero-knowledge certificates.
5Data Verification
The demand side verifies the authenticity of the processed data.
Project Roadmap
Project Launch(Completed)
Duration: 3 months
- Market and technology research
- Release the white paper
Give it a try(In Progress)
Duration: 6 months
- Actively participate in Web3 events to increase visibility
- Start designing and coding with 1 typical cases to verify technical feasibility
Let's make it bigger
Duration: 9 months
- Corporate financing
- Achieve two typical cases based on top-level project parties and market demand.
Commercialization closed loop
Duration: 9 months
- Achieve automated task processing
- Initially forming a complete industrial chain
- Issue tokens and design an economic model
Future
- PrivEcho becomes a global brand
Get in Touch
Request a Demo
Interested in partnering with PrivEcho? Let's schedule a demo.